External Network VAPT: tools, information sources
This is a live post; it will undergo changes, which are captured in change log, provided at the end of this post.

This is a live post; it will undergo changes, which are captured in change log, provided at the end of this post.
Being part of many external VAPT engagements, one thing was clear from outset — methodology is the key, but so are the information sources & tools for conducting the VAPT.
This series is my attempt to record all the tools and information sources that have been helpful to me over the last few years.
Traditionally, external VAPT can be divided into the following major phases:-
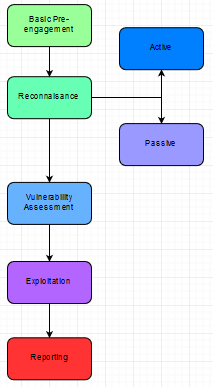
In this article, we will try to cover the first 2 phases — basic pre-engagement & reconnaissance.
Basic Pre-Engagement
It is very tempting to start an external penetration test as soon as customer asks us to. After all, we can perform this test from our current location (no need to travel to customer’s site to perform test) and,
Who cares about that silly thing called documentation? Turns out, except us, everyone.
Your customer wants it so that they can compare, at the end of test, whether the entire perimeter has been accessed or not (in other words, did we leave anything out);
Your boss / management (any other role who is a decision maker in your hierarchy) wants it so that they know we didn’t do more than we were asked to (scope creep is not mythical) & that we did all that we were supposed to;
So, here are the things that one should keep in mind before starting an external penetration test
Scope of work
Is entire perimeter to be tested, or few IP addresses?
Few customers will share the list of external IP addresses to test and won’t be happy if you stray from that list. Few other customers would want you to tell them the attack surface (in other words, what IP addresses of ours are exposed publically) before they give us permission (for full or partial test).
Type of test (black box, grey box, white box)
Black box — we won’t tell you anything about our network, the type of machine under that IP, etc. We want to see what an external attacker would do.
Here, you will have to make it clear that uptime of external IPs are not your responsibility. You will need their IT staff to be on standby during the test so that they can monitor the network and devices for any performance hit. You will be expected to stop when they ask you to.
Grey-box — we will give you some information (e.g., IP address space, type of devices, make / model, etc.).
The expectation here, from customer, usually boils down to one line — now that we told you the things that we have on our external network (and potentially saved you lot of time), what vulnerabilities are we exposed to?
Is physical security testing part of scope?
If it is, i suggest you get your get-out-of-jail card before moving a muscle. Also called “authorization letter”, this document (signed by an authorized signatory — may or may not be the CISO / CIO but the person who is legally authorized to sign agreements on behalf of the company) will help you when you get caught in a mis-understanding with local cops. The coalfire incident has shown how important is this document. So get this before starting the pentest of any service / infrastructure that is business / mission — critical for your customer. TrustedSec has made a host of legal documentation available for no cost (thank you guys!) to facilitate legal boundaries around your physical security pentest. I recommend you have a look at them.
Few more pointers:-
https://www.techrepublic.com/article/dont-let-a-penetration-test-land-you-in-legal-hot-water/
https://www.securitymagazine.com/articles/88489-penetration-testing-by-letter-of-the-law
https://securitycurrent.com/legal-issues-in-penetration-testing/
Report Deadline
Very important. End of testing is different from end of engagement. Testing ends when it ends (!). However, reporting is another, separate activity. Reporting starts after testing is over. You must schedule some time for this.
Preferred timings of test
Some customer would want you to initiate the test when no one is in office (out of working hours). Few customers would ask you to initiate the test during working hours. You have to document this.
Reconnaissance
Wikipedia defines it as
The third definition relates to the objective of network recon. There are 2 major ways to perform recon — one that makes a lot of noise, letting everyone know that you are onto them (active) while the other is more sneaky, stealthy (passive).
Passive Recon
Many people have written lot about it. However, i have few points to mention here:-
Whether you have IP address or a domain name, you need to find ASN (Autonomous System Number) belonging to that company first. The benefit — it will help you find all the IP ranges that belong to the company. You can use below links to find ASN from a domain name or IP address:-
- https://hackertarget.com/as-ip-lookup/
- Networksdb.io
- BGP looking glasses (https://bgp.he.net/)
You would also want to look at sub-domain enumeration. Utilize the following tools
- Amass
- Censys
- Shodan
- Spiderfoot
- Virustotal
- ViewDNS.info
- VHostScan (https://github.com/codingo/VHostScan)
- Google Transparency Report (transparencyreport.google.com)
- CertSpotter
- CertDB
- Crt.sh
Active Recon
This is where we interact directly with the customer infrastructure. The tools that could be utilized in this activity include, but are not limited to, the following:-
- Knock (https://github.com/guelfoweb/knock)
- Fierce
- Sublist3r
- Aquatone
- Nmap
- masscan
So that’s all for now. We will expand on this series soon.



